Hello my friends, I want to discuss Data encryption algorithms which are associated with symmetric key encryption standards. The topic is related to the domain of cybersecurity application systems. The main sources of security encryption technologies are adopted with efficient processing systems and all these are associated with a well-defined application processing system to encrypt data.
Introduction
The data encryption will transfer all the data into the coding algorithm. The access to secret key encryption and decryption are associated with the strong password technique. The encrypted data is referred to as ciphertext, the unencrypted data is defined to be a plain text. Encryption is a popular data structure that is associated with efficient data security methods where all these applications are associated to create a method of standardized security techniques. There are two main data encrypted technologies such as asymmetric and symmetric algorithms.
Functions of data encryption
The purpose of data encryption is deployed to protect digital information and store all the information in computer systems and transmit the information through internet services or other computing network systems. Data encryption methods and standardized protocol are associated with efficient algorithms and this plays a major role in IT system security.
The algorithm provides resources of functionality is which would improve confidential data structures and also enhance all security authentication processing system. The authentication processing system will verify all the messages and provide integrity with proof of message transitions. The applications and non-reputational Data encryption standards will ensure for sending or receiving the messages according to the transmission routing system.
Process of Data encryption algorithm.
The encryption algorithm is associated with the encryption key. The result of the chipper text will allow the user to see the original form of code whenever the decryption process is successfully implemented.
Symmetric key
The symmetric key uses the same secret key of encryption and decryption process in systems for message or file transfer system. The symmetric key encryption is faster than asymmetric encryption system because all the exchange of information’s and keep processing systems are acquired with a quick attack. The company creates a security distributed system where it manages all the sources of encrypting keys and adapts asymmetric algorithms to create an exchange of keys after using symmetric for encryption data.
Click here for Data security issues
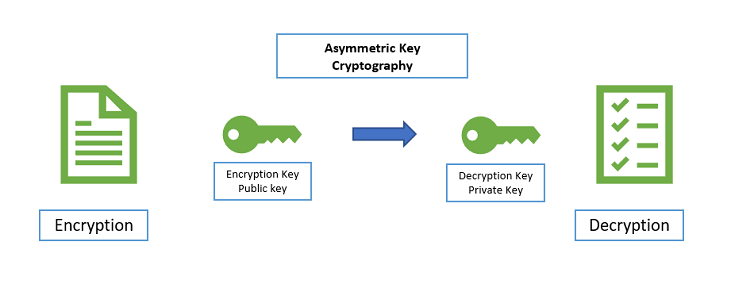
Asymmetric algorithm
The asymmetric cryptography technologies referred to public-key cryptography technologies where it uses one public, one private key method. The private key is associated to protect the data sources. method algorithms are used with cryptographic systems and public key encryption is widely used to secure sensitive data transitions. The RSA algorithms will have public and private encrypted data structures and all these are associated to create confidential integrity and authentication processing system for digitalizing solution sources.
Challenges
Methods of encryption standards are associated with a random key processing system. The key determinants of the possible number of keys are attacked with a plausible key size. The size is increased according to the number of resource techniques and perform all computation system. Break the chip her side-channel attack and cryptographic system. The side-channel attacks are implemented with chip her and create an actual test method. The attacks have attended to succeed with error control systems.
Data encryption solutions
Data protection solutions are deployed with data encryption systems, the application will provide encryption for all devices email and smart applications. The encryption functionalities and all sources of control capabilities of all devices are deployed with a data encryption system. The organization faces all challenges to protectant reduce the data loss in data functionalities. The application and sources of protection of data and preventing loss of information with the use of external devices and removal of media with all web application devices are deployed to improve business opportunities and also create efficient encryption standards. The sensitive data structure is associated with big data technologies and this will provide solutions with efficient data threat reduction methods and also reduce all Malware application processing systems.
The email control and encryption standard are deployed with efficient data loss prevention techniques. Encrypted email systems will provide security methods and have remote workforce technologies. BYOD system applications and data loss prevention are associated with emails and software technologies that are deployed with proactive tag systems. The encryption of sensitive data with a male and attachments is associated to create a solution by deploying automatic warn and block of unauthorized users.
The data encryption standards and complicated processing systems, Data loss prevention technique will handle several data systems and data encryption algorithms will solve all the problems and create efficient encrypted standards for device control systems.
click here for Cloud based solutions
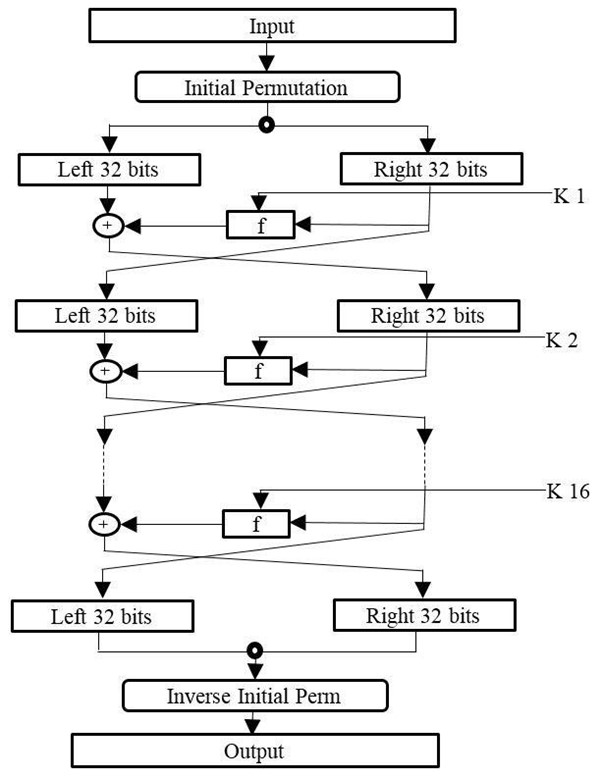
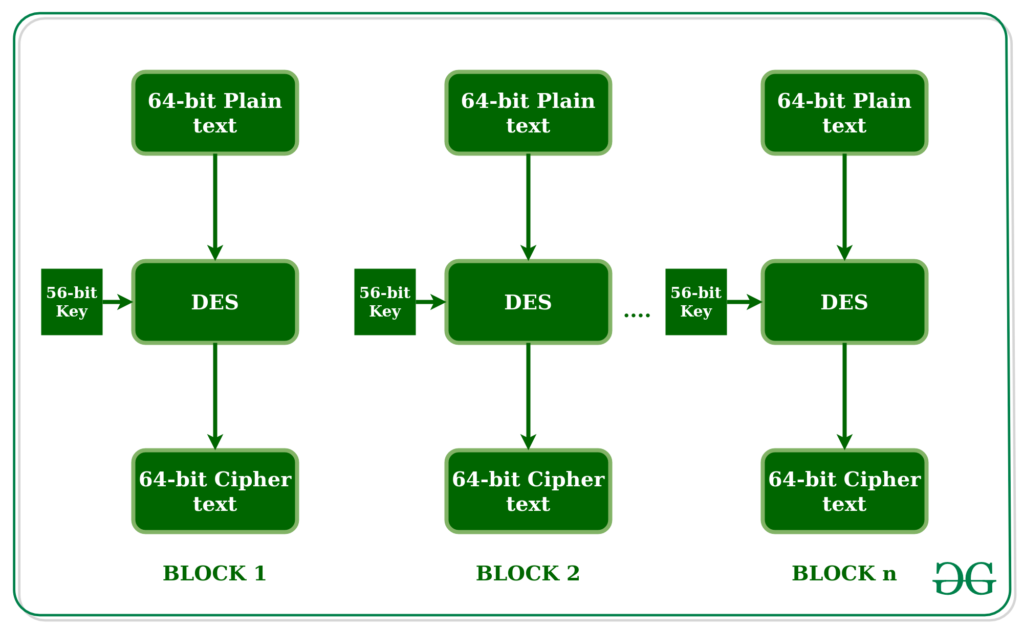
DES Algorithm
The data encryption standards and algorithms are associated with symmetric key block chipper, the algorithm is deployed with plaintext 64bit blocks will convert the entire text using 48-bit keys.
DES all these systems are based on Feistel block chip her. The data encryption system consists of 16 rounds and a Feistel structure, it consists of different keys of each round encryption. The application and approval of federal encryption systems are associated with subsequent data systems and consists of all information security.
NIST replace with DES
The application of NIST is replaced with DES, the 56bit key length was too small, the encryption and consideration of processing powers are associated according to the strength of key size and also create ongoing technological advanced computing systems that are associated with new challenges of encrypted standards.
DES steps
- The algorithm processing systems of 64-bit plain text will block all the permutation functioning systems and allow authorized applications.
- Initial permutations will perform with plain text methods.
- The next level of permutations will increase the application and create two halves of blocks and keys are associated with left plain and right plain text.
- LPT and RPT processing will have 16 rounds of encryption processing.
- LPT and RPT will re-join and create final permutation systems with a combined block.
- 64 bits of chipper text is used to create efficient results.
The application of entire processing technologies of algorithms is divided into five steps.
- Key transformation.
- Expansion of all permutation all data systems.
- S- Box permutation.
- P- Box permutation
- XOR and swap.
Conclusion
In conclusion, all data encrypted algorithms are associated to improve security key sources. There is an electronic codebook, chipper blockchain, chipper feedback, output feedback, counter data transitions where all these methodologies are associated to enhance the mode of algorithms and adopt security sources.

