Introduction

Cyber terrorism is a term used to describe the use of digital technologies to conduct acts of terrorism. This can include using the internet to spread propaganda and incite violence, hacking into critical infrastructure to cause disruption, or conducting cyber-attacks against financial institutions. Cyber terrorists may also use social media to spread their message and recruit new members.
Various security organizations view cyberterrorism and the parties involved differently. The FBI defines cyberterrorism as any premeditated, politically motivated attack against information, computer systems, computer programs, and data by subnational groups or clandestine operatives, resulting in violence against noncombatant targets.
A cyberterrorist strike, according to the FBI, is distinct from a regular virus or denial of service (DoS) attack. A cyberterrorist attack, according to the FBI, is a cybercrime that is specifically planned to do bodily harm. However, governments and the information security community cannot agree on what constitutes a cyberterrorist act. Physical injury is not always required for a cyber strike to be classified as a terrorist act. Cyberterrorism is defined by the North Atlantic Treaty Organization as a cyber strike that uses or exploits computer or communication networks to create “sufficient destruction or disruption to engender fear or coerce a society into an ideological purpose,” according to NATO.
The banking industry, military installations, power plants, air traffic control centers, and water systems are all plausible targets for cyberterrorists, according to the United States Commission on Critical Infrastructure Protection.
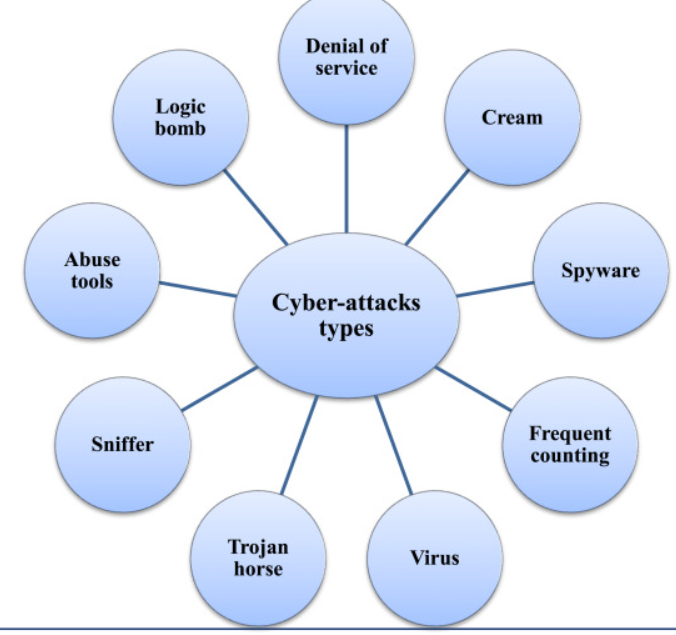
Types of Cyber Terrorism
Cyberterrorism is a type of terrorism that uses computers and the internet to conduct attacks. These attacks can be against individuals, businesses, or even governments. Cyberterrorists may use viruses, worms, spyware, and other malicious software to cause damage or disrupt service. They may also engage in activities like hacking, identity theft, and cyberstalking.
There are many diverse types of cyberterrorism, and each one can have different effects. For example, an attacker could release a virus that deletes files on a victim’s computer. This could cause major financial damage if the victim is a business. Another type of attack could involve taking control of a computer system in order to disable it or steal sensitive information. This could be devastating to a government if critical infrastructure like power plants or air traffic control systems are affected.
Cyberterrorism is a new phenomenon, but it is growing in sophistication and frequency. As increased people and businesses rely on computers and the internet, the potential for damage from these attacks will only increase. It is important to be aware of the diverse types of cyberterrorism so that you can take steps to protect yourself and your business.
Examples of Cyber Terrorism
Cyber terrorism is a growing threat in our increasingly connected world. Here are some examples of cyber terrorism that have occurred in recent years:
1. The WannaCry ransomware attack in 2017 infected more than 230,000 computers in 150 countries, causing billions of dollars in damage. The attack used a vulnerability in Microsoft Windows to encrypt files on victims’ computers and demand a ransom for the decryption key.
2. In 2016, hackers associated with the Islamic State (ISIS) took over the Twitter account of the U.S. Central Command and used it to post threatening messages. They also released sensitive military information, such as the names and addresses of service members.
3. In 2015, hackers breached the computer systems of the U.S. Office of Personnel Management and stole the personal information of more than twenty-two million people. The hackers, who were linked to the Chinese government, gained access to sensitive information such as social security numbers and fingerprints.
4. In 2014, hackers breached Sony Pictures’ computer systems and released confidential information, such as employee social security numbers and salaries. The hackers also released several unreleased films and caused severe damage to Sony’s computer systems.
Legislation on Cyber Security
There is currently a lot of discussion about how to best protect against cyber terrorism. Some believe that the government should create and enforce strict laws and regulations around cyber security, while others believe that this would be an infringement on personal liberties.
One argument for stricter legislation is that it would provide better protection against cyber-attacks. Currently, there are many ways for hackers to exploit vulnerabilities in computer systems, and there is no sure way to prevent all attacks. However, if the government were to create laws requiring companies to take certain steps to secure their systems, it would make it much more difficult for hackers to successfully attack. This would in turn make it less likely that cyber terrorists would be able to use these methods to wreak havoc.
Another argument for stricter legislation is that it would help to prevent future attacks by deterring would-be hackers. If it were clear that there were severe penalties for anyone caught engaging in cybercrime, it is possible that fewer people would attempt to conduct such attacks. This could help to reduce the number of successful cyber terrorist attacks in the future.
Prevention From Cyber Terrorism
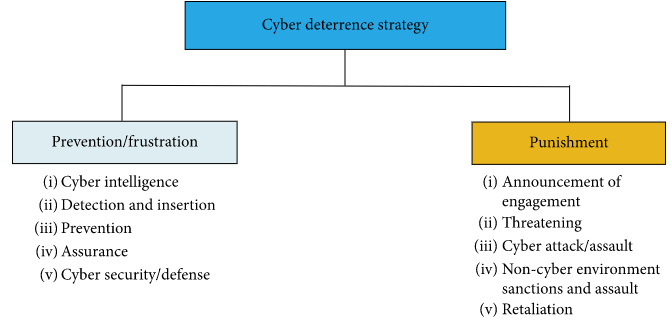
When it comes to cyber terrorism, prevention is key. There are a few things you can do to prevent yourself from becoming a victim of cyber terrorism. Firstly, make sure that your computer and mobile devices are up to date with the latest security patches. This will help to protect your devices from being exploited by hackers. Secondly, use strong passwords for all of your online accounts and make sure to change them regularly. Thirdly, be vigilant about what you click on online and only download files from trusted sources. And finally, keep a backup of all your important files in case of a ransomware attack. We can use cyber deterrence strategy as well to control it.
Conclusion
Cyber terrorism is a serious threat that we face in today’s world. With the increasing reliance on technology, increased people are vulnerable to cyber-attacks. It is important to be aware of the dangers of cyber terrorism and to take steps to protect yourself and your family from these threats. Cyber terrorists are constantly evolving and finding new ways to attack, so it is important to stay up to date on the latest news and developments in the field of cybersecurity.
