Before discussing cryptographic computation let us know what Cryptography actually is. We live in a century where the efficiency of Technology is unlimited. Day-to-day, the developments in the Technology sector are sky-rocketing. Now, we have some common platforms such as Facebook, Instagram, WhatsApp, etc. And tomorrow this list will go boundless. As the technology accelerates, it is also important to take the next step into the term “Security”.
Consider the possibility that a middleman intercepts messages sent between you and your partner. What would your reaction be? To counteract this, a hero is known as “cryptography” has arisen. Cryptography? Let’s take a closer look.
CRYPTOGRAPHY
The science of data encryption and safekeeping of a user’s sensitive data such that only the intended receiver can retrieve it. Your data can be classified into two types. Data that is accessible without any special measures is called Plaintext
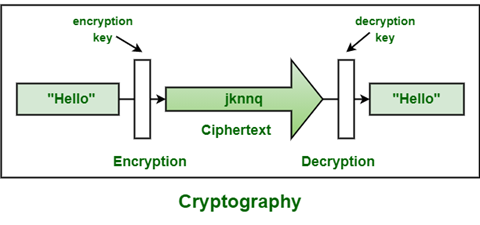
Fig. Link: https://media.geeksforgeeks.org/wp-content/uploads/20210224215653/fgfdgrfgrf21.png
For example, a mobile without locks], while if plain text data is disguised to hide the information using algorithms is called Encryption [noticed a “phrase messages and calls are end-to-end encrypted”?].
So, when we decode the encrypted message, we call it Decryption. Cryptographic security is an information security tactic, highly used in enterprises to secure their companies’ information. In other words, it is the mastery of concealing information from an unauthorized person using a company’s data.
HOW DOES CRYPTOGRAPHY SECURE DATA?
Cryptographic security secure information and communication details using rigid concepts and rule-based calculation called ALGORITHMS. These algorithms are hard to untangle (decode). Currently, cryptographic security is used in key generation, digital signing, cyber-security, mobile authentication, data privacy, browsing on the Internet, credit card transactions, and email. This mode of security satisfies confidentiality, integrity, authentication, and non-reputation.
HOW CRYPTOGRAPHY IS CONFIDENTIAL?
A cryptographic system guarantees that only those with the right clearance can retrieve your information. It safeguards the privacy of users whose personally identifiable data is stored in this manner. Encryption is a promising method of ensuring that data is safe and secure. And it gives users the impression that their privacy is protected.
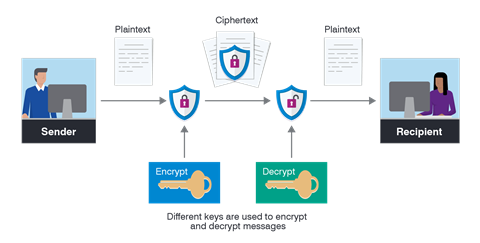
Fig. Link: https://www.proofpoint.com/sites/default/files/what-is-encryption.png
Encryption:
Even if an unauthorized individual has figured out how to decrypt the encryption, the information is meaningless unless they have the appropriate key (which could be a phrase number or word).
We have two forms of encryption in terms of encryption: symmetric encryption and asymmetric encryption. Now let’s take a look at what it is about!
SYMMETRIC ENCRYPTION:
Symmetrical encryption, also known as Secret-key, single-key, shared-key, and one-key encryption, is one of the oldest methods of encryption. It is employed when the sender and receiver have the same key to decode the encryption.
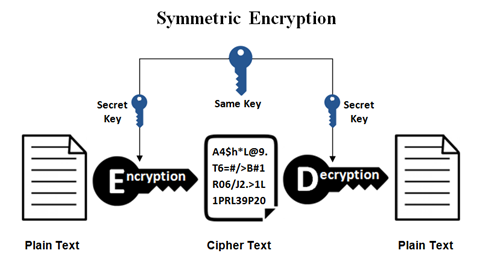
Fig. Link: https://www.ssl2buy.com/wiki/wp-content/uploads/2015/12/Symmetric-Encryption.png
How does it work?
Symmetric Encryption employs a Secret Key, which makes it impossible for third parties to decrypt the data.
To create an effective and efficient key, a Random Number Generator is used.
In symmetrical encryption, the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES) are extensively used encryption algorithms.
Asymmetric Encryption is more complicated, smoother, and slower than Symmetrical Encryption.
Data sent with symmetric key encryption is less safe and vulnerable.
To send symmetrically encrypted communications, you only need a small amount of electricity and a simple technique.
The cipher code of the symmetrically encrypted message is either the same or
smaller than the original message.
Application of Symmetric Encryption:
- Payment sector (banking transactions).
- Hashing (Random Number Creation)
- Validation
- Symmetrical Encryption
ASYMMETRIC ENCRYPTION:
When the sender and the receiver have more than one key to decrypt the information. This can be termed Symmetrical Encryption, also known as public-key.
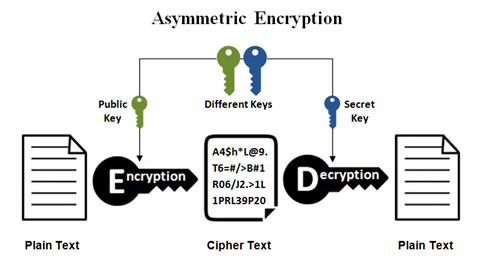
Fig. Link: https://www.ssl2buy.com/wiki/wp-content/uploads/2015/12/Asymmetric-Encryption.png
How does it work?
A public key will be used by the sender, and a private key will be used by the receiver. As a result, they won’t have to manually lock or open the door. Some of the protocols that use HTTPS for Asymmetric Encryption include Transport Layer Security (TLS) and Safe Sockets Layer (SSL). Asymmetric encryption ensures that information sent is somewhat secure. It consumes more energy than expected. It also outperforms symmetrical encryption in terms of efficiency.
Applications of Asymmetric Encryption:
- Digital Signing for authentication.
- Encrypted connection between website and browsers.
- Mail Encryption.
Fig: Asymmetrical encryption
IT ENSURES INTEGRITY
“Integrity” refers to the fact that the data and the information system are both genuine, which is ensured via hashing techniques and message digests. By employing codes and digital keys to confirm that the communication received is genuine and sent by the intended recipient. For example, if a sender says “Hi,” you’ll get “Hi,” not “Bye,” and the message you get is from the person you expected. The stored data does not become mixed up with other data during the continual transfer of information.
THE SENDER AND RECEIVER ARE THE RIGHT ONES
One of the most critical jobs is to ensure that both the sender and the receiver are correct (the beginning and end of information are right). The best method to do this is through authentication! To access information, you’ll need a unique key, such as a username and password. Now there are some advanced methods such as retina scanning, voice recognition, fingerprint scanning, and facial recognition.
Fig: Authentication
NON-REPUTATION
Insecurity sector, non- reputation describes that neither the sender nor the recipient can renounce the fact of sending or receiving information. These data are made proof using Digital Signature.
AVAILABILITY OF DATA
A person can retrieve their deleted or lost data with the right permission using the system. So, the data is reliable and accessible.
AT WHAT LAYER THIS CRYPTOGRAPHIC SECURITY IS IMPLEMENTED IN
COMPANIES’?
Cryptographic security is typically applied in Transport Layer Security (TLS), SSL, HTTPS, and other protocols. The Application layer, which is the most prevalent, protects data from being hacked twice if the first layer of data is compromised.
CRYPTOGRAPHIC SECURITY AND CRYPTOCURRENCY
The growing popularity of cryptocurrencies has prompted crypto enthusiasts to seek out “Cryptographically Secured Currency” in order to maintain a secure blockchain and ensure that the Crypto coin is issued by the proper authorities.
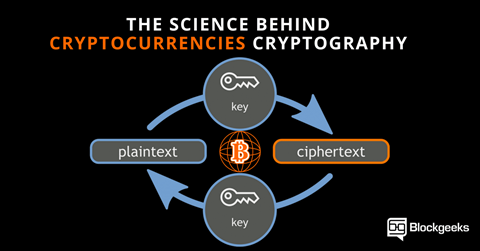
Fig. Link: https://www.ssl2buy.com/wiki/wp-content/uploads/2015/12/Asymmetric-Encryption.png
As a result, cryptographic security is unavoidable in protecting and securing personal and corporate data from cyber dangers and cyber-attacks.
