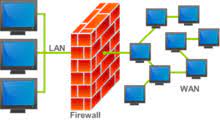
COMPUTER FIREWALL
A computer firewall is a network security device that analyses incoming and outgoing network traffic and determines whether specific traffic should be allowed or blocked based on a set of security rules. A firewall is a piece of software or firmware that protects a network against illegal access. It uses a set of rules to evaluate incoming and outgoing communications in order to identify and block threats.
Firewalls are used in both personal and business contexts, and many devices, including Mac, Windows, and Linux PCs, come with one built-in. They’re usually regarded as an important part of network security. For more than 25 years, firewalls have served as the first line of defence in network security. They create a barrier between secure and controlled internal networks that can be trusted and untrustworthy external networks like the Internet.
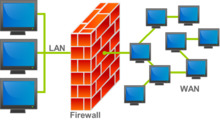
Are firewalls important?
Yes, Firewalls are significant because they influenced modern security techniques and are still widely used.
To inspect traffic and mitigate threats, most devices employ firewalls or closely related tools. They first appeared in the early days of the internet, when networks required new security methods to deal with increasing complexity. Since then, firewalls have become the foundation of network security in the client-server model, which is the central architecture of modern computing.
TYPES OF FIREWALL’S:
The two types are network-based and host-based, when categorising them by what they protect. Network-based firewalls, which are frequently hardware, protect whole networks. Host-based firewalls, which are frequently software, protect particular devices known as hosts.
When categorizing by filtering method, based on their overall structure and mode of operation, firewalls can be classified into numerous categories. Some of the important and most used firewalls are,
- PACKET- FILTRING FIREWALLS:
Packet-filtering firewalls, the most basic and oldest type of firewall architecture, essentially generate a checkpoint at a traffic router or switch. Without opening the packet, the This firewall does a rudimentary check of the data packets going through the router, evaluating information such as the destination and origination IP addresses, packet type, port number, and other surface-level information.
Although the transport layer is used to retrieve the source and destination port numbers, this packet-filtering firewall primarily works on the network layer of the OSI reference model. It examines each packet separately and has no way of knowing whether or not it is part of a larger stream of traffic.
2. CIRCUIT LEVEL GATEWAYS:
Circuit-level gateways are a form of simple firewall that works by checking the transmission control protocol (TCP) handshake. They are designed to allow or deny traffic fast and easily without taking a lot of CPU resources. This TCP handshake check verifies that the packet originates from a valid session.
These firewalls do not verify the packet itself, while being incredibly resource-efficient. So, if a packet included malware but had the correct TCP handshake, it would be allowed to flow. This is why circuit-level gateways alone are insufficient to secure your organisation.

(Image reference: https://www.youtube.com/watch?v=Iax00ra2hpk)
3. STATEFUL INSPECTION FIREWALLS:
Stateful inspection Firewalls are also known as dynamic packet-filtering firewalls, evaluate both incoming and outgoing communication packets over time. This type keeps track of all open connections using a table. When new packets arrive, it compares the information in the packet header to the state table’s list of valid connections to see if the packet is part of the current connection. If this is the case, the packet is allowed to pass without additional scrutiny. If the packet does not match a previously established connection, it is examined using the new connection rule set.
From the time a connection is established until it is terminated, it keeps track of all activities. Filtering decisions are made using both administrator-defined rules and context, which refers to utilising data from earlier connections and packets belonging to the same group connection.
4. PROXY FIREWALLS:
- This type may also be referred to as Application-Level Gateways/Cloud Firewalls. Proxy firewalls filter incoming traffic between your network and the traffic source at the application layer, hence the name “application-level gateway.” A cloud-based solution or another proxy device is used to offer these firewalls. Rather than allowing traffic to connect directly, the proxy firewall creates a connection with the traffic source and inspects the incoming data packet.
- This type allows security engineers to have more granular control over network traffic since it checks the content of the payload. It can, for example, allow or disallow a single incoming Telnet command from a specific user, whereas other types can only manage generic incoming requests from a certain host.
- The ability to block specific content, such as known malware or specific websites, as well as recognize when certain applications and protocols, such as Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), and domain name system (DNS), are being misused, is the primary benefit of application layer filtering.
- If proxy firewalls have one disadvantage, it is that they can cause significant slowdown due to the extra steps in the data packet transfer process.
5. NEXT GENERATION FIREWALL:
This type combines the previous types with additional security software and devices. The advantage of an NGFW is that it combines the strengths of each type while covering the weaknesses of each type. An NGFW is frequently a collection of technologies grouped together under one name, rather than a single component.
Deep packet inspection (checking the data packet’s actual contents), TCP handshake checks, and surface-level packet inspection are some of the more common features of next-generation firewall architectures. Other technologies, such as intrusion prevention systems (IPSs) that seek to automatically thwart assaults on your network, may be included in next-generation firewalls.
The problem is that there is no universal definition of a next-generation firewall, so it’s crucial to double-check what features these firewalls offer before purchasing one.
6. HARDWARE FIREWALLS:
Hardware firewalls capture data packets and traffic requests before they reach the network’s servers using a physical device that functions similarly to a traffic router. Physical appliance-based firewalls, such as this one, excel at perimeter security by intercepting hostile traffic from outside the network before it reaches the company’s network endpoints.
A hardware-based firewall’s biggest flaw is that insider assaults can easily get through it. Furthermore, the actual capabilities of a hardware firewall may differ depending on the manufacturer for example; some may have a lower capacity for handling simultaneous connections than others.
7. SOFTWARE FIREWALLS:-
Any form of firewall that is put on a local device rather than a separate piece of hardware is referred to as a software firewall (or a cloud server). A software firewall’s main advantage is that it may be used to create defense in depth by isolating individual network endpoints from one another. Individual software firewalls on separate devices, on the other hand, might be complex and time-consuming to maintain. Furthermore, not all devices on a network may be compatible with a single software firewall, necessitating the deployment of multiple software firewalls to protect all assets.
If you are still not sure how and what firewall to use for your issues, don’t worry, You can easily get “Computer Repair Onsite (CROS)” help by clicking here. where a team of experts will address your issues and solve them in no time.

FIREWALL ATTACKS:
Firewalls are an essential component of every company’s cybersecurity strategy. Firewalls, on the other hand, should never be considered the be-all and end-all of your company’s cybersecurity demands. Yes, firewalls are essential, but there are a few drawbacks that make it unwise to rely solely on this security solution to secure your company.
Here’s a quick rundown of firewall attacks,
- Insider attacks:
Internal firewalls can be used to partition the network and provide internal protection in addition to perimeter firewalls. NGFW characteristics can be used to audit sensitive information if an attack is suspected. All audits should be held to a standard set by the organization’s baseline documentation, which describes best practises for using the network.
Firewalls, on the other hand, can be useful even when the attack originates within your network. If you have internal firewalls in addition to perimeter firewalls, Internal firewalls aid in the partitioning of individual assets on your network, making it more difficult for attackers to move from one system to another. This extends the attacker’s breakout time, giving you more time to respond to the attack.
2. Missed Security Patches:
When network firewall software isn’t correctly handled, this problem can develop. As with any other piece of software, there are flaws that attackers can exploit. This is true of firewall applications as well. When firewall providers uncover these flaws, they normally work quickly to develop a patch that addresses the issue. The most effective solution to this problem is to establish and adhere to a disciplined patch management schedule. According to this plan, you (or the person in charge of your cyber security) should check for any and all firewall software security updates and make sure to deploy them as soon as feasible.
3. Patching/Configuration issues:
A poorly configured firewall or a vendor update that is missed can be detrimental to network security. IT administrators should be proactive in keeping their security components up to date. Even if your network has a firewall and all of the latest vulnerability patches, it can still cause problems if the firewall’s configuration settings cause conflicts. In some cases, this can result in a decrease in network performance, while in others; a firewall may fail to provide protection.
4. Distributed denial of service (DDos) attacks:
This is a common attack strategy characterized by high effectiveness and low execution cost. The basic goal is to overwhelm a defender’s resources, resulting in a shutdown or prolonged inability to provide services. Protocol attacks of one type are designed to deplete the resources of firewalls and load balancers, preventing them from processing legitimate traffic. There is no simple solution to DDoS attacks because there are numerous attack strategies that can exploit various weaknesses in your company’s network architecture. Some cyber security service providers provide “scrubbing” services, in which they redirect incoming traffic away from your network and separate legitimate access attempts from DDoS traffic.
FIREWALL VENDORS
Businesses intending to buy a firewall should be aware of their requirements and have a good understanding of their network architecture. There are numerous types, features, and vendors that specialist in those various types, but the best and trusted one and only one place is to buy the hardware and software related accessories is x-tech buy just by ordering it in https://www.xtechbuy.com/ .

Before you begin fixing a firewall or troubleshooting any problem, you should have a good understanding of what the problem is, how it arose, what’s that affecting. To know everything about solving these kind of issues you can click here.