Hackers do not normally inform their sufferers that they have been hacked. Most of the time, whilst hackers benefit access to computer systems to do their grimy work, they do not need anybody to realize. That way, they can come back yet again to peer for what else they are able to do or find. Because of that, you may not realize in case your pc has already been hacked. But there are a handful of symptoms and signs that suggest a hacker might also additionally have invaded a community or a pc you use. Some are pc-associated, and a few are not. If any of those sound familiar, possibly you have been a victim without understanding it. And if that is the case, it is higher which you realize approximately it, so you can take short action. If you think you are hacked, then it’s most advisable to contact a computer expert like CROS.
Signs that you got hacked!
You get a ransomware message
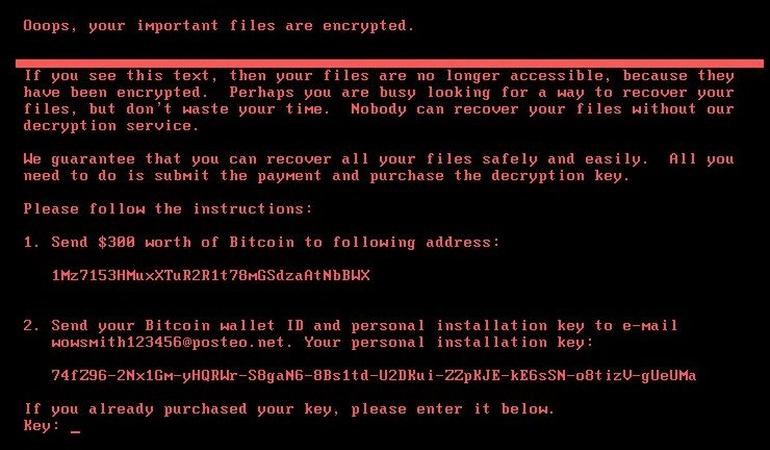
One of the most exceedingly terrible messages anybody can see on their PC is an abrupt screen assume control over revealing to them all their information is scrambled and requesting an instalment to open it. Ransomware is immense! After a slight decline in action in 2017, recover asking programs returned thundering. Billions of dollars in efficiency is being lost and billions in emancipate are being paid. Private ventures, huge organizations, clinics, police headquarters and whole urban communities are being brought to a stop by ransomware. About half of the casualties pay the payoff, guaranteeing that it is not disappearing at any point soon. Shockingly, as per cybersecurity protection firms who are regularly associated with the payouts, paying the payoff does not bring about working frameworks about 40% of the time. Turns out that ransomware programs are not without bug and opening unpredictably scrambled connected frameworks is not as simple as placing in an unscrambling key. Most casualties end up with numerous long periods of vacation and extra recuperation steps regardless of whether they do pay the payment.
Solution: To begin with, in the event that you have a decent, later, tried information reinforcement of the affected frameworks, you should simply re-establish the included frameworks and completely confirm (formally called unit testing) to ensure the recuperation was 100%. Tragically, most organizations do not have the incredible reinforcements that they thought they had. Test your reinforcements! Try not to let ransomware be the first one to run through your organization’s basic reinforcements. In case of a doubt, the businesses should call up some one like Benchmark IT Services and the home users can connect with someone like “CROS“.
The best security is to ensure you have great, dependable, tried, disconnected reinforcements. Ransomware is picking up refinement. The troublemakers utilizing malware are investing energy in undermined undertaking situations figuring how to do the most harm, and that incorporates scrambling or debasing your ongoing on the web reinforcements. You are facing a challenge if you do not have great, tried, reinforcements that are unavailable to vindictive gate crashers. If you wish to buy some advanced security tools, you can visit X-Tech Buy.
If you have a place with a record stockpiling cloud administration, it most likely has reinforcement duplicates of your information. Try not to be excessively sure. Not all distributed storage administrations can recoup from ransomware assaults, and a few administrations do not cover all document types. Consider reaching your cloud-based document support and clarify your circumstance. Now and again technical support can recuperate your documents, and a greater amount of them, than you can yourself.
You get a fake antivirus message
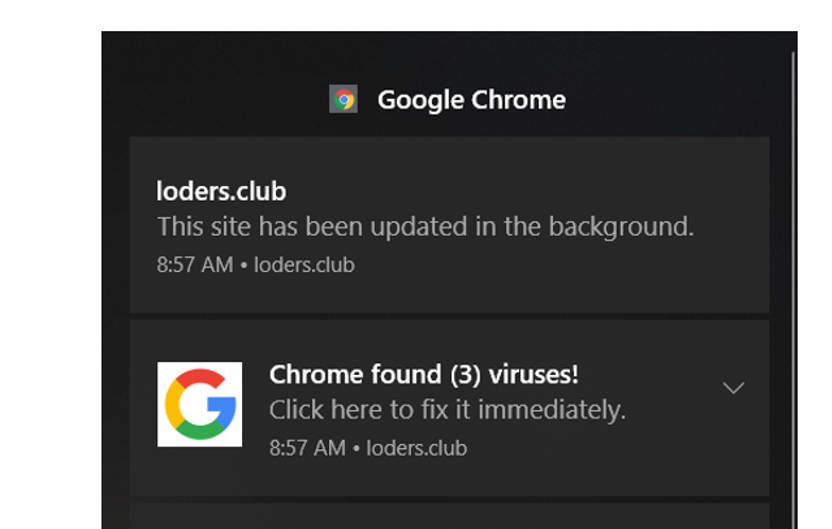
You get a popup message on your PC or cell phone that it is infected. The pop-up message claims to be an antivirus filtering item and is indicating to have discovered at least twelve malware diseases on your PC. Although this is not close as well-known as it used to be, fake antivirus cautioning messages are yet a circumstance that must be managed in the correct manner.
They can happen in view of two reasons: Either your framework is now undermined, or it is not undermined past the pop-up message. Trust in the last mentioned. These kinds of fake antivirus messages typically have made sense of an approach to bolt up your program so you cannot escape the fake message without killing the program and restarting it.
You have unwanted browser toolbars

This is a typical indication of exploitation: Your browser has various new toolbars with names that appear to demonstrate the toolbar should support you. Except if you perceive the toolbar as originating from a notable vendor, it is an ideal opportunity to dump the counterfeit toolbar.
New programs abruptly show up. You did not get it or introduce it, yet you notice another program has been stacked onto your PC. That is a reasonable sign that somebody has controlled your PC.
A trusty secret key does not work. On the off chance that a secret key out of nowhere quits working, that could mean a programmer has broken into your PC and changed your record’s login subtleties—and it could deteriorate from that point.
You observe unexpected software installs. Undesirable and surprising programming introduces are a major sign that your PC has been hacked. In the beginning of malware, most projects were PC infections, which work by adjusting other real projects. They improved shroud themselves. Most malware programs these days are Trojans and worms, and they regularly introduce themselves like authentic projects. This might be on the grounds that their makers are attempting to walk a flimsy line when the courts get up to speed to them. They can Endeavor to state something like, “However we are an authentic programming organization.”
The undesirable programming is regularly legitimately introduced by different projects, so read your permit understandings. Regularly, I will read permit understandings that clearly express that they will introduce at least one different project. At times you can quit these other introduced programs; here and there you cannot.
What should you do if you get hacked?
Isolate Your Computer
To cut the association that the programmer is utilizing to “pull the strings” on your PC, you must isolate it so it cannot impart on a system. Segregation will keep it from being utilized to assault different PCs just as keeping the programmer from proceeding to have the option to acquire documents and other data. Pull the system link out of your PC and mood killer the Wi-Fi association. On the off chance that you have a PC, there is frequently a change to kill the Wi-Fi. Try not to depend on doing this through programming, as the programmer’s malware may reveal to you something is killed when it is truly still associated.
Shutdown and Remove the Hard Drive
If your computer is compromised, you need to shut it down to prevent further further harm to your documents. After you have controlled it down, you should haul the hard drive out and interface it to another PC as an optional non-bootable drive. Ensure the other PC has exceptional enemy of infection and hostile to spyware. You should probably also download a free spyware expulsion instrument or free too kit recognition scanner from a respectable source like Super AntiSpyWare or Malwarebytes.
Backup Your Important Files from the Previously Infected Drive
You will need to get all your own information from the recently contaminated drive. Duplicate your photographs, records, media, and other individual documents to DVD, CD, or another clean hard drive.
Wipe Your Old Hard Drive
Regardless of whether infection and spyware checking uncover the danger is gone, you should in any case not believe that your PC is malware free. The best way to guarantee that the drive is totally perfect is to utilize a hard drive wipe utility to totally clear the drive and afterward reload your working framework from trusted media.
After you have sponsored up the entirety of your information and put the hard drive back in your PC, utilize a protected circle eradicate utility to totally wipe the drive. There are many free and business plate delete utilities accessible. The plate wipe utilities may take a few hours to totally wipe a drive since they overwrite each area of the hard drive, even the unfilled ones, and they regularly make a few goes to guarantee they did not miss anything. It might appear tedious however it guarantees that no stone is left unturned and it is the best way to be certain that you have wiped out the danger.
Reload the Operating System From Trusted Media and Install Updates
Utilize your unique OS circles that you bought or that accompanied your PC, do not utilize any that were replicated from elsewhere or are of obscure source. Utilizing trusted media assists with guaranteeing that an infection present on corrupted working framework circles does not reinfect your PC. Make a point to download all updates and fixes for your working framework before introducing whatever else.
Reset All Passwords & Set Up Multi-Factor Authentication
Regardless of whether your online records have not been messed with, it is yet a smart thought to reset every one of your passwords. In a perfect world, you should think of solid passwords, and ensure you utilize an alternate one for each record. Likewise, to support their security, you should transform them consistently.
Adjacent to that, you should empower any type of multifaceted validation on your records. The standard is two-factor validation, where you must utilize an arbitrarily created code on your telephone to finish the login cycle. That way, regardless of whether a programmer figures out how to take your secret key, he/she will not have the option to get to your records.
Nonetheless, if your records are as of now undermined, it is ideal to make new ones without any preparation. It is an issue; however, it is a lot more secure.
Your CPU/GPU Is Being Used at Full Capacity
Unwanted and unexpected software installs are a big sign that your computer has been hacked. In the early days of malware, most programs were computer viruses, which work by modifying other legitimate programs. They did this to better hide themselves. Most malware programs these days are Trojans and worms, and they typically install themselves like legitimate programs. This may be because their creators are trying to walk a very thin line when the courts catch up to them. They can attempt to say something like, “But we are a legitimate software company.”
The unwanted software is often legally installed by other programs, so read your license agreements. Frequently, I will read license agreements that plainly state that they will be installing one or more other programs. Sometimes you can opt out of these other installed programs; sometimes you cannot.
To make things somewhat simpler, consider buying a USB drive caddy to place your hard drive in to make it simpler to associate with another PC. If you do not utilize a USB assist and select to interface the drive inside rather, ensure the plunge turns on the rear of your drive are set as an auxiliary “slave” drive. If it is set to “ace” it might attempt to boot the other PC to your working framework and everything serious trouble could become unavoidable once more.
If you do not feel good eliminating a hard drive yourself or you do not have an extra PC, then you might need to take your PC to a respectable nearby PC repair shop like “Computer Repair Onsite” (CROS). For the businesses though, we recommend contacting BITS who are pros in resolving such issues.

