Hello my friends, as technology is increasing day by day, many viruses attack the functionality of computerized services. I want to discuss about the topic related to securities and malware where encrypting viruses are clearly determined. The subject is taken from cybersecurity and malware applications. In this blog, I am going to discuss about all functionality is related to encrypting viruses.
Introduction
Cybercriminals use encrypted ransomware and this is a type of application that is difficult to crack the encryption and remove malware application system. The computer consists of all the personal information and encrypted with malicious code from ransomware. The ransomware applications are associated with advanced encryption techniques and ras encryption, it is difficult to do another incredible application and cracked the user application system.
All the files are encrypted in the application of computerized data sources by the virus will decrypt all the keys and steal sensitive information. This application is carried out by clicking on unauthorized links, and applications which are to download particular web services.
The file consists of scam applications and need not pay for the decryption processing system because the infected files will take over computerized to systems and this is affected by encrypted virus systems. The applications and identification of ransomware will define file coder and also have encrypted files which will specify specific encryption standard and also try for decryption when we want to access the sources of an application system.
Function of encryption is simple
Checksum and decryption technologies are operated to have efficient calculation systems where or logic keys are associated to create functionality with a various encrypted standard. Most of the applications and the number of users are interconnected to generate efficient outputs and analyze all types of malware applications because it is necessary to recover all the files from encrypt of algorithms which will change the original code into encrypted code to provide security. The encryption keys and cryptographic algorithms are associated to display efficient security processing systems and followed by move files with progress technologies.
Problem
The problem is associated with encryption standards after moving the virus into the deployed application system. The antivirus will encrypt the data and provide securities such that it is not enabled to decrypt the file with our unauthorized users. The file encryption and ransomware technologies will affect the entire network connections such that their applications and the data technologies cannot be detected and remove antivirus until you create an efficient application processing structure.
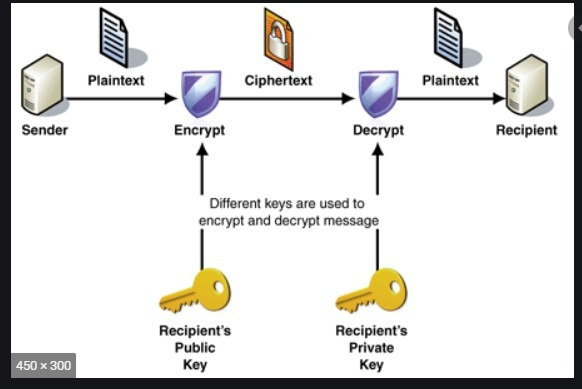
Symmetric algorithm
The symmetric algorithm technologies will use the same keys as encrypted technologies where all these are deployed and used with decryption techniques. Asymmetric encryption technologies will create a secure and form of encryption systems where all the private keys are deployed with public-key methods. The other part of encryption will have a public key and create a description with unique private keys.
Click here for any Data security issues
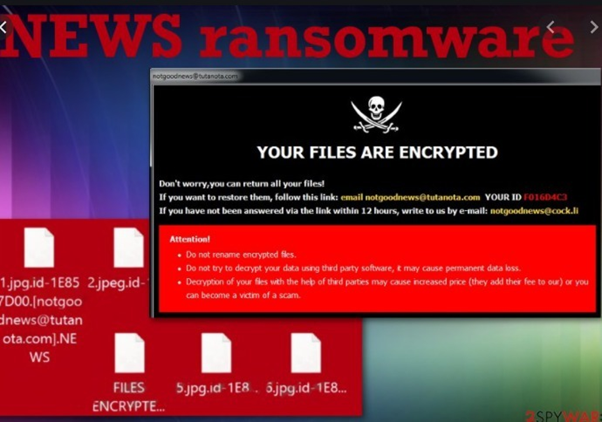
Ransomware
The ransomware applications will take public key source methods and embedded with executable files, the sources of encrypting technologies and keys are associated with passwords with efficient random numbers. The encrypted technologies and ransomware technologies will encrypt the sources of data that are associated with text and passwords with random numbers.
The brute force attacks and decrypt technologies of viruses are affected by itself and also try to restore all encrypted keys. The technical perspective of inscriptions is associated with virus and anti-malware applications and security tools are not restored with encryption of files and remove the damaging attacks in the existing computing platform. The ransomware attacks and android devices will increase massive applications and enhance cyber-criminal attacks which are faced by many of the people and it is needed to create awareness regarding smartphone attacks which are associated with encryption of viruses technologies.
The anti-virus scanning applications can easily detect the virus and creates an efficient security system. Simple encrypting viruses are acquired and virus code methods but scanning will be started and detected with static decryption routine systems. The virus responds to all the configuration data structures which are created between different encryption or decryption routine algorithms and all these mechanisms are associated to create a response with antivirus vendors and also have wildcards that can approve system to detect all the virus attacks in existing encryption processing system.
The virus encryption or decryption technologies are associated with random routines or polymorphic application system. The first polymorphic virus is associated with the dark avenger mutation engine. The mutation engine will permit 1 virus and have millions of different decryption technologies and these applications will not allow any antivirus vendors to detect the coding processing system. The application should be supervised to improve emulated encrypted standards which will logically specify the computing structures and detect all errors in the existing zone.
Click here for Cyber security issues
Next-generation random encryption
The next-generation random encrypted coats are called metamorphism. The metamorphism viruses will change the entire code on the fly and create efficient exchange instructions according to random hosting or virus technologies. The applications will have a collection of data through random pickup and deployed it with garbage instruction technologies were hosting or collecting of information are accessed in different virus techniques and create infection processing system. The scanning engine should be changed and the updated engine should support antivirus research technologies where metamorphic code can detect all the sources. The criteria and risk factor of polymorphic and metamorphic code will give advanced research technologies which will enhance applications and the virus can won’t able to detect malware application processing system.
Prevention methods
- The application should create efficient backup systems where all the important files are stored in backup techniques.
- Avoid access to personal information with email or SMS data transmission.
- Use of repeatable antivirus or internet security should reduce.
- Firewalls with repeated techniques should not be encouraged.
- Create a trustworthy VPN.
Conclusion
A virus uses encrypted standards to hide the applications from the virus scanner. The encrypted virus full jumble all the program code and create a difficulty to recognize the main function. Encryption of virus code begins with decryption of algorithms and continuous scrambled or encrypted court will remind virus systems and analyze the infected applications with the encoding of technologies. The main source of encryption standards is associated to reduce the attacks.

