Abstract
The web application technologies and analysis of SQL injections are associated to analyse all attacks and create exploration with web-based application technologies. The exploitation and web-based application systems are authorized with SQL injection attacks where all the tricks are associated with the server to gain methods where the authorization of illegal access credentials is associated with the SQL query method. The SQL injection methods and all the attackers are caused to classify the information according to the primitive venerable attack systems where different classifications and analysts are associated to avoid the cause of SQL injection.
Introduction
SQL injection methodologies will explore all web-based technologies and the injection statements are associated with input string methods and gain unauthorized access which is interlinked with database SQL injection methodologies. All the vulnerabilities and risk propagation technologies are associated with high-level risk management technologies their ability to manage all database queries are associated with a web-based application and create the frontend and backend operations which are supposed with firewall technologies. The application of SQL injections creates an advantage of insecure code and adopts all the validation of attacker such that an authorized user could not access the SQL query commands and only the authorized users can access the network application protocol.
Objective
The main objective of SQL injection attack methodologies is associated to run the harmful code which would relieve the confidential information where all the SQL methodologies are conducted to create unauthorized access with database management systems and enhance the security of database techniques.
First order injection attacks
The first-order injection attacks are authorized according to the receiver information technologies and all these fundamentals are deployed to produce desired results according to the response of application technologies.
Second order injection method
The second-order injection attack methodologies will analyse the malicious code management technologies where all these applications are deployed into an application by an attacker management system. The malicious code injection techniques will attack the authorised applications and inserted into database techniques. All the indirect trigger technologies of Qila method are associated with input and output functionalities where all the attacks are associated to create efficient data transfer flow. The capability of injections will leave the job of functionalities which could analyse the job of detection and prevention mechanism.
lateral injection methods
The lateral injection attack techniques are associated to compress oracle database systems where all remote controlling methods and data types are included with the number of input and output functionalities according to the consideration of coding management system.
Blind SQL injection attack
The web applications and all winnable attack systems are associated with SQL injections and create a result of data systems. The application and display functionalities of all credentials are accessible to create a logical statement of injected SQL statements in the webpage systems and allow all the threats against the database technologies to define a statement with injection methods.
Common vulnerabilities
The common vulnerabilities are associated with SQL injection systems where all the browsers will send malicious input data to service and check for executive malicious SQL query management systems. Cross site scripting data structures are allocated to steal the sensitive information and create honest data management system.
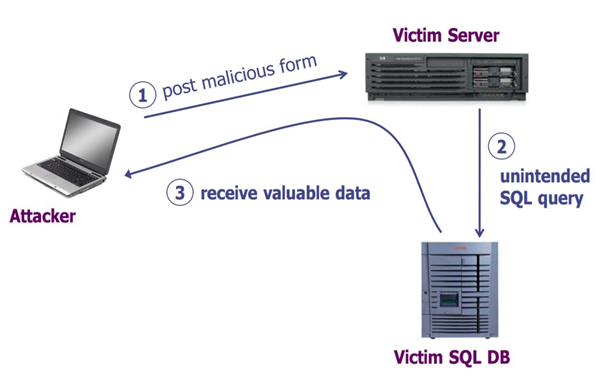
SQL in web page
The SQL injection of core technologies will destroy the entire database management system, supplication is commonly used in hacking techniques and place the malicious code in SQL statements with the webpage input data structure.
- The SQL injection methods are carried out with efficient input and output technologies where the username and user ids are used instead of name and id because it gives an efficient statement that will clearly deploy the database management functionalities.
- The capability is select the statement is associated with a variable user-id switch are attached with string and passwords which are used with variable management functionalities.
- The SQL injection methodologies are used in common database exploitation systems where all the injections and vulnerable attacks are associated to summarise the application technologies which are interlinked with SQL management.
Impact of SQL injection
The successful injection of SQL attacks is associated to create unauthorised access to the sensitive data structures and steal the product information like password and credit card information system. Tamanna abilities and high-profile data breaches are associated to create efficient results with SQL injection data structures where all the reputations and damage of regulatory systems are deployed to create an action which could be presented with back door management functionalities.
- Retrieving hidden data from modifications of data systems are acquired through SQL query management system.
- Subverting data transitions with logical data structures are associated to improve the credential access abilities were all the functionalities and data sources are associated to improve the extraction of data structures which is all the structural analysis are carried out with attack management system.
click here for any Cyber Security issues
Retrieving hidden data
In SQL injection methodology it is necessary to retrieve hidden data and display all characterization of data systems by clicking on the web browsers will create unique URL output systems.
- SQL queries of database systems are equipped with all detail management system.
- The capability of product tables is associated according to the characterization of height product techniques.
- The capability of SQL query functionalities are associated with subverting application systems.
Threat modelling system
- SQL injections will allow all the attackers to identify spoof identification and causes issues which will avoid voiding transactions.
- The capability of disclosure of data information services and destroying of data will analyse the transition of an available data structure.
- SQL injection methods are generally used in PHP and asp application technology.
- There are several SQL methods which are associated according to skill and imagination database systems where all the countermeasures are associated to have a privilege of connections between database server management techniques.
Prevention of SQL injection
The capability of SQL injection technologies is executed with possible malicious SQL statements where all the statements of database server within web application technologies are associated according to the bypass of security measures where all the authentication and authorisation of web pages are associated to retrieve the information and create a server management technology which could add, modify and delete records of the database system.

