In recent years, Incognito mode has become a common feature in most browsers. While the incognito mode is often called private browsing, there are still many ways to track your actions while using incognito mode. However, many people have no idea regarding this fact and mistakenly believe that incognito mode allows them to browse the internet anonymously and there is no possible way to track them.
What does incognito mode actually do?
When selecting the option for opening a new incognito or private window, a new special window will be opened. This browsing window can still be used normally to browse the internet, the difference lay in the fact that all the browsing history, cookies, and a few other information will be deleted from inside your device once the incognito mode is ended or the browsing window is closed. What this means ultimately is that when someone else is using the same device later, your browsing history from that session is not shown. So, the protection that incognito mode offers is mainly focused on protecting the user against other users of the same device.
In some cases, private browsing might be able to temporarily browse without being monitored through cookies. This is due to a feature of incognito mode that prevents cookies from the main session to be used in the incognito browsing session. Cookies is the term used to refer to small files used by browsers to help improve the browsing experience, a common example would be store password to enable automatic login. However, the advertising industry has found many ways to exploit cookies to better track browsing behavior to develop a more comprehensive profile about the user. This profile will be very useful in categorizing the type of advertisement the user might be susceptible to and use those advertisements to sell more products to the user.
There are also some added benefits of cookies separation. The first one is to allow the user to log into multiple accounts at the same. Another benefit is to bypass the paywalls that some website that employs to attract more visitors. These websites allow people to browse a limited number of pages, once the limit is exceeded they can no longer browse anymore content, and to proceed further they need to do some things such as signing up or even pay for it. While some of these websites are very advanced, some of them can be misled using private browsing mode and allow the user to refresh their page limit count.
What incognito mode CANNOT do
However, incognito mode comes with many limitations that many people are unaware of. The most crucial difference that people get wrong is the fact that they believe it can hide the activity data across the network. However, in reality, the user browsing activity is still visible to the internet service provider or ISP and network administrator such as the university and company IT department.
Another common misconception is regarding login. When the user login to a website that tracks their online activity, those data will remain safely stored by those websites and private browsing will not make any difference. A common example is that many people believe that even if they are logged into their Google account, their search queries will not be saved. While it is true that the device will not show evidence of the search, Google can still track it from their record.
There is also a dangerous misconception that poses a serious threat to cybersecurity, which is that fact that private window protects against virus and malware. This stems from the fact that when incognito mode is closed it will delete the browser’s download history, and many forget that the file itself is still inside the computer. So if the infected file can somehow get inside the computer, ending the browsing session will not delete these files. Another Limitation of private browsing is that private browsing itself can be ignored if the computer being used is infected by malware that monitors network traffic because these things record the browser activity in places that the browser does not have access to. That is why even if people use private browsing, it is still important to make sure that they use good quality security software, especially one from a reputable provider such as X-Tech Buy.
Other common misconceptions include believing that a website that is bookmarked when using incognito mode will not be saved and get deleted when the bookmark window is closed. Many people also believe that incognito mode makes it impossible to trace the user location. It is important to understand these limitations to avoid problems that might be caused by browsing irresponsibly.
Conclusion
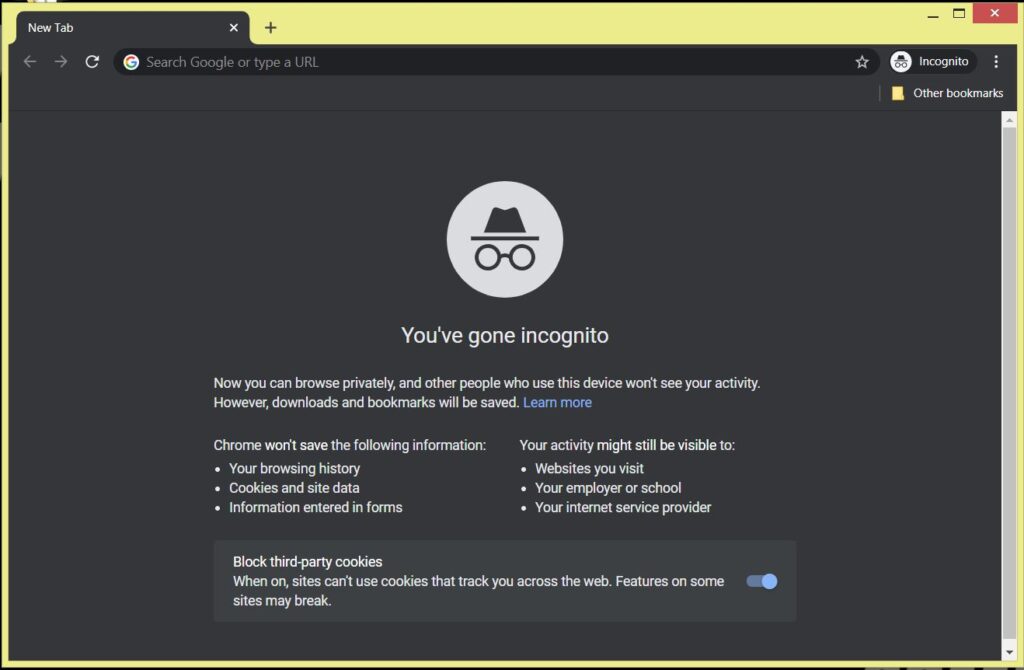
In conclusion, Incognito browsing might be referred to as private browsing, but in reality, its ability to provide privacy is very limited. It is still important for the user to maintain a responsible browsing practice in order to safely browse the web. Additionally, many browsers developers have tried to explain the limitations of incognito mode. For example, when opening a new incognito window chrome will lightly outline some of the limitations of incognito mode and provide a link for a short but informative article, it is the user’s responsibility to make sure they understand what they are doing. It is also a good idea to directly consult with cybersecurity experts such as BITS.
On the other hand, experiencing a private browsing session might be harder to achieve. The most basic requirement of conducting private browsing is to do it without any third party observing those actions and in the current society, many parties have the ability to monitor network traffic activity as mentioned before. However, there are still some things that can be done to improve privacy such as using VPN or Virtual Private Network products. Although this can prevent network administrators to monitor your activity, it requires some time and money investment to determine which product is the right fit for each user. A harsher method is to disable JavaScript from the browser, which unfortunately will drastically lower the quality of the browsing experience.

