Cybersecurity, usually called information security, ensures integrity, confidentiality, and accessibility (ICA) of data. Cybersecurity involves a combination of tools, risk management approaches, technology, training, and benchmarks constantly changing to secure networks, devices, programs, and data against attacks or unauthorized access. Businesses and governments now keep this data on computers and send it to other computers via networks. Devices and their underlying systems have flaws that, if exploited, can seriously compromise a firm’s health and goals. For any firm, a data breach may have a range of severe repercussions. It may damage a company’s reputation.
Furthermore, non-compliance with legal provisions might impact business sales as a result of a data breach. A data breach is expected to cost an affected business $3.6 million on average. For small and medium enterprises, Cybersecurity is a significant worry. Since the flare-up of the COVID-19 pandemic and the subsequent “Work from Home” reality that it has set up all through the world, network safety chances have expanded considerably more than previously. If businesses want to stay afloat in the face of cyber assaults in 2021, they’ll have to get a sound cybersecurity strategy and a competent incident response plan. Cyber-criminals sophistication was and continues to be on the rise.
Cyber Security Classification:
For Corporate Organizations
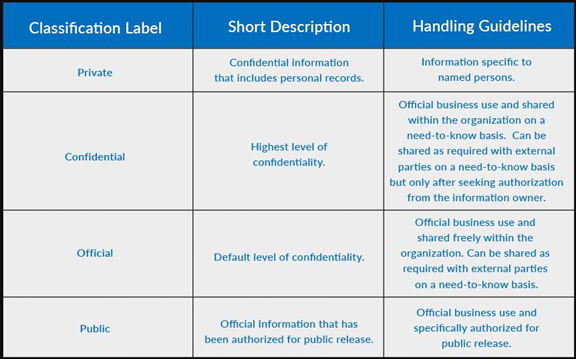
Fig. link: https://www.cyberstash.com/uploads/article/Information-security-corporate-organization.png
For Governments
Every country has its way of handling and classification. The local government follows the guidelines provided by the state government.
Types of threats of Cybersecurity
Cybercrime can be broadly classified into two types:
A) Network-related or device-related crimes like viruses or malware.
B) Crimes using devices to participate in criminal activities like Identity theft or phishing.
Let’s now know a little more about various threats,
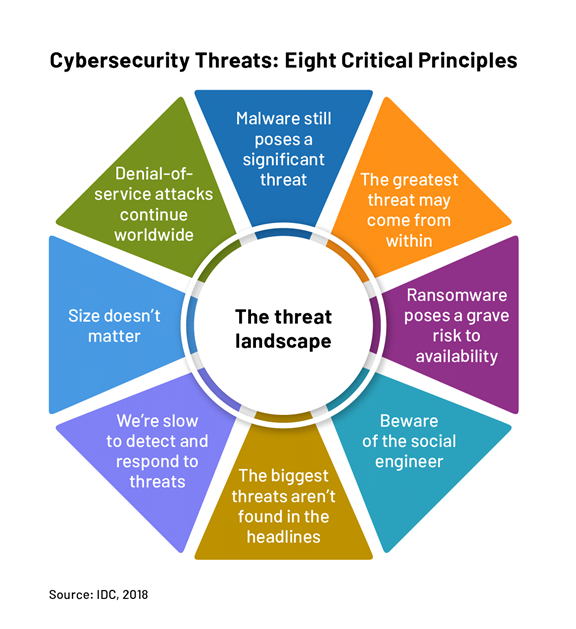
Fig. Link: https://dome9.com/wp-content/uploads/2018/07/D9_The-Threat-Landscape_R1-1.png
Malware: The program that conducts a malicious operation on a specific device or network, such as corrupting data or gaining control of a machine. Malware may be included in app downloads, mobile websites, phishing emails, and text messages by attackers.
Trojans: The Trojan is a form of malware that enters a target system appearing like something else, such as a regular piece of software, but then releases harmful code once inside the host machine. This is named after the Trojan Horse of ancient Greek history.
Phishing: A well-known and trustworthy name is used to deliver a malicious link through message or email, which, when clicked, renders the system susceptible and may be exploited to steal sensitive data.

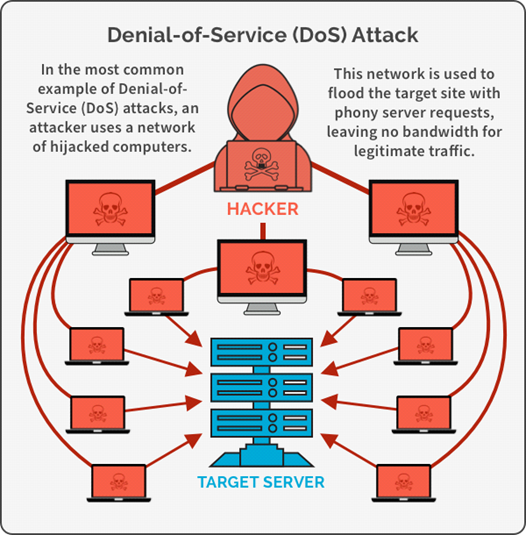
DDoS: The attacker commences this attack by taking down the network by flooding its traffic from many different sources. There is a lot of software capable of doing so. They are used to send an outrageous number of requests resulting in site failure, and once the network is down, it becomes easy to hack into the system.
Ransomware is one of the worst malware programs, locking files with powerful encryption after infecting the system. The cybercriminal(s) behind the assault would then demand a ransom in exchange for an encryption tool or key after encrypting the files. It is nearly hard to decode data with solid encryption without a decrypting key or tool.
Social Engineering: It uses psychological tactics to convince users to commit security mistakes or reveal sensitive data. Social engineering assaults are carried out through a series of phases. To carry out the assault, a perpetrator first analyses the target victim to acquire required background information, such as potential avenues of entry and weak security procedures. The attacker attempts to win the victim’s confidence and offer stimuli for later acts that violate security protocols, such as disclosing sensitive information or providing access to vital resources.
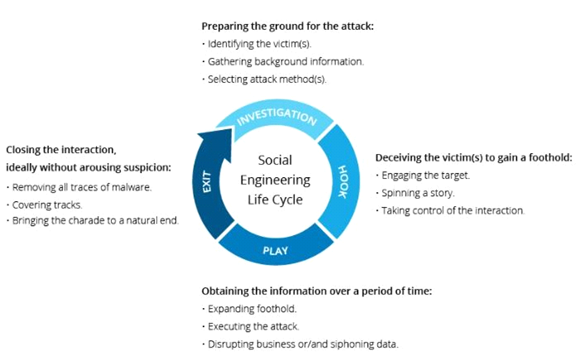
Fig. Link: https://www.imperva.com/learn/wp-content/uploads/sites/13/2019/01/social-engineering.png.webp
Troubleshooting
Steps to remove ransomware:
- Immediately disconnect the affected device from all wired or wireless connections, including the Internet, network, mobile devices, external drives, cloud storage accounts, and network drives. This prevents the ransomware from spreading to other devices. It also checks whether any devices connected to the infected device have been infected by ransomware. If the ransom has not been requested, delete the malware from the system immediately.
- Knowing what kind of ransomware infected a device can help you take remedial measures. If device access is blocked like Locker ransomware, it may not be possible. Infected devices may need to be inspected by skilled security professionals or diagnosed using software tools.
- Before restoring the system, the ransomware must be removed. During the first hacking attack, ransomware infects the system and encrypts files, and prevents system access. Only the password or decryption key can unlock or decrypt the restriction.
Several ways of removing ransomware –
- Check whether the ransomware has been removed. Ransomware sometimes deletes itself after infecting the system; in other cases, it stays on one device to infect other devices or files. Use anti-malware/anti-ransomware. Seek the help of a security expert. Cooperate with internal or third-party technical support security experts to help you remove ransomware that was manually deleted. If possible, check the software installed on the device and uninstall the ransomware file. This is only recommended to experienced security experts.
- Restore files by restoring to the previous version of the operating system that existed before the attack. If the backups are not encrypted or locked, use the system restore function to restore them. Please note that any files created after the last backup date will not be converted.
Measures to avoid Cyber-attacks
- As one of the oldest methods to solve network security problems, antivirus software should be a breeze. However, many computer users do not install it or fail to update the software they own. First, install reputable and effective antivirus software on each laptop and desktop computer. When antivirus software asks you to download an update, please don’t ignore it. Viruses, spyware, and malware move very fast, so antivirus software needs constant updates to stay ahead. Download any updates now to ensure you are protected from the latest cyber security threats.
- Set up a firewall in your home or business to protect your network and computer from external attackers. These devices can be in hardware or software format, which can filter out unnecessary traffic very effectively. A hardware firewall can be placed between your computer and the modem to prevent malicious code or viruses from entering. A software-sized firewall can be installed on almost any operating system, and it can also effectively protect network security risks from the computer or network attacks.
- If you use the Internet in a cafe or hotel/airport, it is best to use a VPN to protect yourself. WIFI security in these public places may be poor. A VPN helps protect your Internet connection to encrypt data going in and out of your computer.
- In the event of a cyber-attack, you’ll also require a robust cyber incident response strategy. It should be a document that outlines the six critical steps of an incident response strategy. It should spell out the procedures that all workers must follow in the event of an attack.
- You’ll need the appropriate security software to keep your organization functioning efficiently. Invest in antivirus, anti-spam filters, and anti-spyware software, and make sure they’re up-to-date. Remove any unnecessary extensions or applications.
