EVERYTHING ABOUT VPN:
What is VPN?
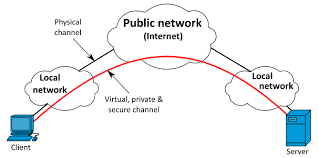
A VPN (Virtual Private Network) allows you to connect to another network securely via the Internet. VPN’s can be used to access Geo-restricted websites, protect your browsing behavior on public Wi-Fi from prying eyes, and much more. VPN’s are quite popular these days, but not for the reasons for which they were invented. Initially, they were simply a technique to securely connect business networks over the internet or to allow you to access a corporate network from your home. VPN’s essentially forwards all of your network traffic to the network, which is where features like remote access to local network resources and circumventing Internet censorship, come into play. The vast majority of operating systems are equipped with integrated VPN support.

In its most basic form, a VPN connects your PC, Smartphone, or tablet to another computer (referred to as a server) located someplace on the internet, allowing you to browse the internet using that computer’s internet connection. So, if the server is in another nation, it will appear as if you are from that nation, and you may be able to access things you wouldn’t ordinarily be able to.
Why VPN?
When you connect to the internet, your ISP normally sets up your connection. It uses your IP address to track you. Your network traffic is routed through the servers of your Internet service provider, who can log and display everything you do online. Although your Internet service provider may appear to be trustworthy, it may disclose your surfing history with advertising, the police or government, and/or other third parties. Cyber criminals might also target Internet service providers: Your personal and confidential information may be compromised if they are hacked. This is especially critical if you use public Wi-Fi networks frequently. You never know who is watching your online activity or what they might steal from you, such as passwords or personal information.
How does VPN works?
Microsoft created the Virtual Private Network (VPN) in 1996 as a mechanism for remote employees to securely access the company’s internal network. After it increased corporate productivity, other businesses began to follow suit. Corporate VPNs that enable remote work are becoming commonplace in the global business world. Developers discovered that this secure “tunnel” could be used by ordinary individuals who wanted to connect safely to the world’s greatest network: the internet. In the consumer industry, VPNs have become the cornerstone of internet privacy.
A VPN first routes your traffic through a VPN server instead of send your internet traffic (such as your online searches, uploads and downloads) directly to your Internet Service Provider (ISP). This way your data appears to come from the VPN server, not from your own device when it’s finally transferred to the Internet. Your IP address a unique number for your home network — is visible on the internet, without a VPN. A VPN masks your IP address through inter-mediation and transformation of your traffic. It also adds encryption to your connection or a tunnel around your identity. The VPN server and encoding tunnel combination block your ISP, governments, hackers and anyone
Different types of VPN’S:
There are four primary types of VPNs currently in use in the market, and the majority of people utilise them:
- Remote access VPN:
A remote access virtual private network (VPN) encrypts all traffic sent and received by users working remotely, allowing them to safely access and use programmes and data stored in the company data centre and headquarters. The remote access VPN accomplishes this by constructing a “virtually private” tunnel between an organization’s network and a distant user, even if the user is in a public area. Because the traffic is encrypted, any eavesdropper will be unable to understand it. Remote users can safely connect to and utilise their company’s network in the same manner they would if they were in the office.
2. SSL VPN:
Not every firm employee has access to a business laptop that they can use to work from home. Many organisations encountered the challenge of not having enough equipment for their staff during the corona crisis in Spring 2020. Using a personal device (PC, laptop, tablet, or phone) is frequently used in these situations. In this instance, businesses rely on an SSL-VPN solution, which is often implemented through a dedicated hardware box. An HTML-5-capable browser, which is used to access the company’s login page, is normally required. Browsers that support HTML-5 are available for almost every operating system. A username and password are required to gain access.
3. Site to site VPN:
A site-to-site VPN is a private network designed to conceal private intranets and allow users of these secure networks to share resources. If your organisation has numerous sites, each with its own local area network (LAN) connected to the WAN, this can be used (Wide Area Network). Site-to-site VPNs are also beneficial if you have two independent intranets and wish to communicate files across them without requiring users from one intranet to access the other. VPNs are primarily used in major corporations. They are difficult to set up and do not provide the same level of flexibility as SSL VPNs. They are, nevertheless, the most efficient means of ensuring communication within and between huge organisations.
4. Client to server VPN:
It’s as if you’re using an extension cord to link your home PC to the company when you use a VPN client. Employees can use the secure connection to connect to the company network from their home office and operate as if they were in the office. A VPN client must, however, be installed and set on the computer first. The user establishes a direct connection to the internet through his/her VPN provider rather than through his/her own ISP.
This essentially cuts the VPN journey’s tunnel portion in half. Instead of creating an encryption tunnel to mask an existing internet connection, the VPN can automatically encrypt data before it is available to the user. This is a type of VPN that is becoming more popular, and it is especially handy for suppliers of unsecured public WiFi. It protects the network connection from third-party access and compromises data encryption all the way to the supplier. It also prohibits ISPs from viewing data that is left unencrypted for whatever reason, and it circumvents any limits on the user’s internet access (for instance, if the government of that country restricts internet access).
Benefits of VPN:
A VPN connection hides your online data transmission and protects it from prying eyes. Anyone with network access and a desire to see unencrypted data can do so. Hackers and cyber thieves are unable to decode this data when using a VPN.
Some of the important reasons to use VPN are,
- Using public networks: Wi-Fi networks in public places, such as coffee shops, airports, and other public places, are extremely dangerous. All it takes is one hacker connected to the same network to easily spy on all your activity. A VPN acts as an invisibility cloak, concealing everything you do on your phone or computer.
- Change of locations: VPN servers simply work as proxies on the internet, allowing you to hide your location. Your exact location cannot be established since the demographic location data comes from a server in another nation. Furthermore, most VPN providers do not keep track of your activity. Some providers, on the other hand, keep track of your actions but do not share them with third parties. This means that any possible record of your user behaviour will be completely erased.
- Secure encryption: An encryption key is required to read the data. In the event of a brute force attack, a computer would take millions of years to decrypt the code without one. Even on public networks, your online activities are masked with the help of a VPN.
- Access to regional web material: Access to regional web content is not always available from all locations. Content on services and websites is frequently restricted to various regions of the globe. To establish your location, standard connections use local servers in the nation. This means you won’t be able to access content from your home while on the road, and you won’t be able to access overseas content from your home. With VPN location spoofing, you can change your location by connecting to a server in another country.
- Secure data transfer: You may require access to important files on your company’s network if you work remotely. This type of data necessitates a secure connection for security reasons. A VPN connection is frequently required to obtain access to the network. To limit the risk of data leakage, VPN services connect to private servers and use encryption methods.
Drawbacks of using VPN:
There are several drawbacks to using a VPN, like with any sort of technology.
- Blockage: Some businesses are catching on to the idea that VPNs allow their users complete control over their content access. Companies are beginning to limit access from recognised VPN IP addresses as a form of retaliation. VPNs, not to be outdone, can just switch on fresh IP addresses to deceive them once more.
- Speed: When you connect to a VPN, your online traffic goes through more steps than usual, which could result in a noticeable slowdown. Developers have taken notice because this has always been the most common issue with VPNs. Many have succeeded in enhancing speed and performance to the point that their VPN users may watch and game without interruption. Also, take a look at our additional tips for speeding up your VPN connection.
- Cookies: While a VPN can keep your data secret and encrypted, it can’t disable cookies, which are sometimes required for websites to function properly. Tracking cookies, which are the evil kind of cookies, can be saved in your browser and used to identify you. Thankfully, tracking cookies are easy to remove.
- Privacy: While a VPN shields you from your ISP, governments, hackers, and other prying eyes, the VPN provider can monitor your online behaviour if they so desire. That’s why picking a reputable service that doesn’t retain logs is so crucial like “BENCHMARK IT SERVICES”.
SOLUTION:
VPN has evolved into a necessary tool for gaining unrestricted access to the internet. Despite the fact that VPN tools have become increasingly sophisticated, you will still encounter a number of issues, which fortunately have solutions. In this article, we’ll go over some of the most common VPN issues and how to solve them using various methods.
There are some steps to follow if we encounter any issue with the VPN,
- Examine the firewall
- Use the help feature to get assistance
- Experiment with the Open VPN protocol
- Remove any previous VPN software from your device
- Determine whether the VPN is compatible with the site or service
- Change the VPN Server
- Experiment with a different VPN Protocol
Doing all of this on your own is difficult and risky, so the best solution is to seek professional advice. There are a few nice, easy options if you’re just getting started with VPNs and want a basic VPN to use on public Wi-Fi networks or to access region-restricted websites. It is simple for a top-rated company like “BECNCHMARK IT SERVICES” to perform it for you.

Because they have faster speeds and a lot more features than the ordinary VPN service, including apps for practically any device—you can even acquire a router with their VPN client pre-installed. All these is done in a simple and sophisticated manner starting by logging in their website, https://www.benchmarkitservices.com.au
CONCLUSION:
A virtual private network (VPN) creates a secure connection between you and the internet. All of your data traffic is routed over an encrypted virtual tunnel via the VPN. When you access the internet, this masks your IP address, making its location invisible to everyone. External attacks are also protected by a VPN connection. That’s because the data in the encrypted tunnel can only be accessed by you – and no one else can because they don’t have the key.
You can access regionally prohibited content from anywhere in the world using a VPN. Many streaming services are not available in all countries. You can still use the VPN to gain access to them. Many VPN connections for smartphones are now available, allowing users to keep their mobile data traffic private. The Google Play Store and the iOS App Store are both good places to look for certified providers. However, keep in mind that utilizing a VPN merely anonymity and protects your internet data traffic. Hacker attacks, Trojans, viruses, and other malware are not protected by a VPN connection. As a result, you should use a third-party anti-virus program.
if you need any type of software or hardware related to vpn’s, we can get all types in the top most shoping place i.e. “XTECHBUY” just by buying them here.

If you need help using the tools or stuck using these you can simply get help from “Computer Repair Onsite (CROS)” from their website here. here we get the solution for all the technical issues from the team of experts.

